The Shadow Mode
Your digital camouflage shield when things get serious.
Have you found vulnerabilities with JOUO? Then take a deep breath - and go into shadow mode: before the vulnerability becomes a threat, we encapsulate your affected systems. Inconspicuously, without interrupting operations - and with maximum protection.

Shadow mode is like a camouflage shield
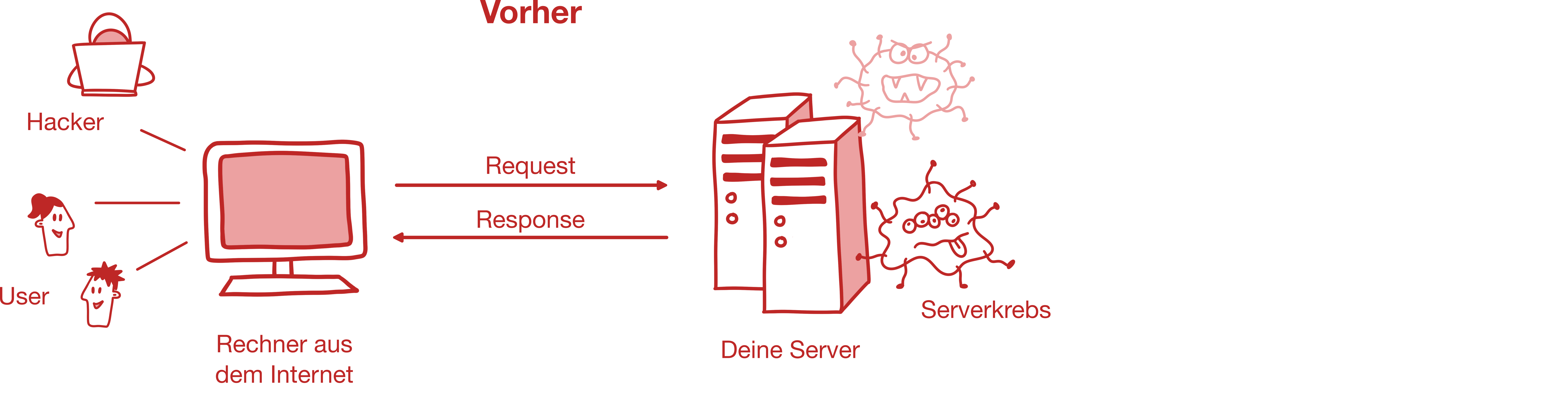
An upstream reverse proxy protects you from prying eyes from outside. Attackers cannot see what is vulnerable. You gain valuable time for remediation - without risk, without panic.
When do you need shadow mode?
-
If you have discovered critical vulnerabilities
-
If your IT teams need time to make clean improvements
-
If you cannot risk someone from the outside recognizing the gaps
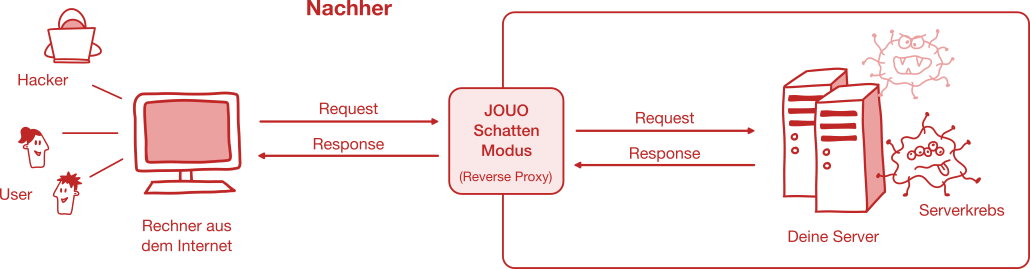
How it works:
-
We place a reverse proxy in front of your systems.
-
The proxy filters and disguises incoming requests.
-
Vulnerable services remain invisible - until you are ready.
Better prevention than an incident
Want to know if you are visibly vulnerable right now? Then book your diagnostic appointment now
Activate shadow mode - how to protect yourself immediately
Have you found vulnerabilites with JOUO? That's good! Now it's time to keep calm and take action. To prevent these loopholes from being exploited from the outside, we switch on shadow mode for you - quite simply with a reverse proxy.
The procedure

Diagnosis by JOUO
- Our scan reveals where your systems are vulnerable.
- You receive a report with clear measures.

Shadow Mode: Reverse Proxy
- An upstream reverse proxy conceals your vulnerable systems from potential attackers.
- Let attacks go nowhere - while you patch in the background.

Fix in peace
- Without panic and with our support, you remove the vulnerabilites.
- No downtime, no PR disaster, no hectic rush.
- Let attacks come to nothing - while you patch in the background.

Back to normal operation
- As soon as everything is clean, we deactivate shadow mode.
- Your infrastructure is tougher, better and safer than before.
What does a reverse proxy do?
A reverse proxy sits like a bodyguard in front of your systems. It receives requests, filters them, encrypts them and only forwards what is not critical - or what you allow. Internal systems remain invisible and protected.
